(Disclosure: ScanGov is a project I maintain with my son.)
ScanGov released a new indicator that assesses how federal and state government websites fare on basic cybersecurity practices.
The scans grade on adoption of Content Security Policy, HTTP Strict Transport Security, X-Content-Type-Options and security.txt.
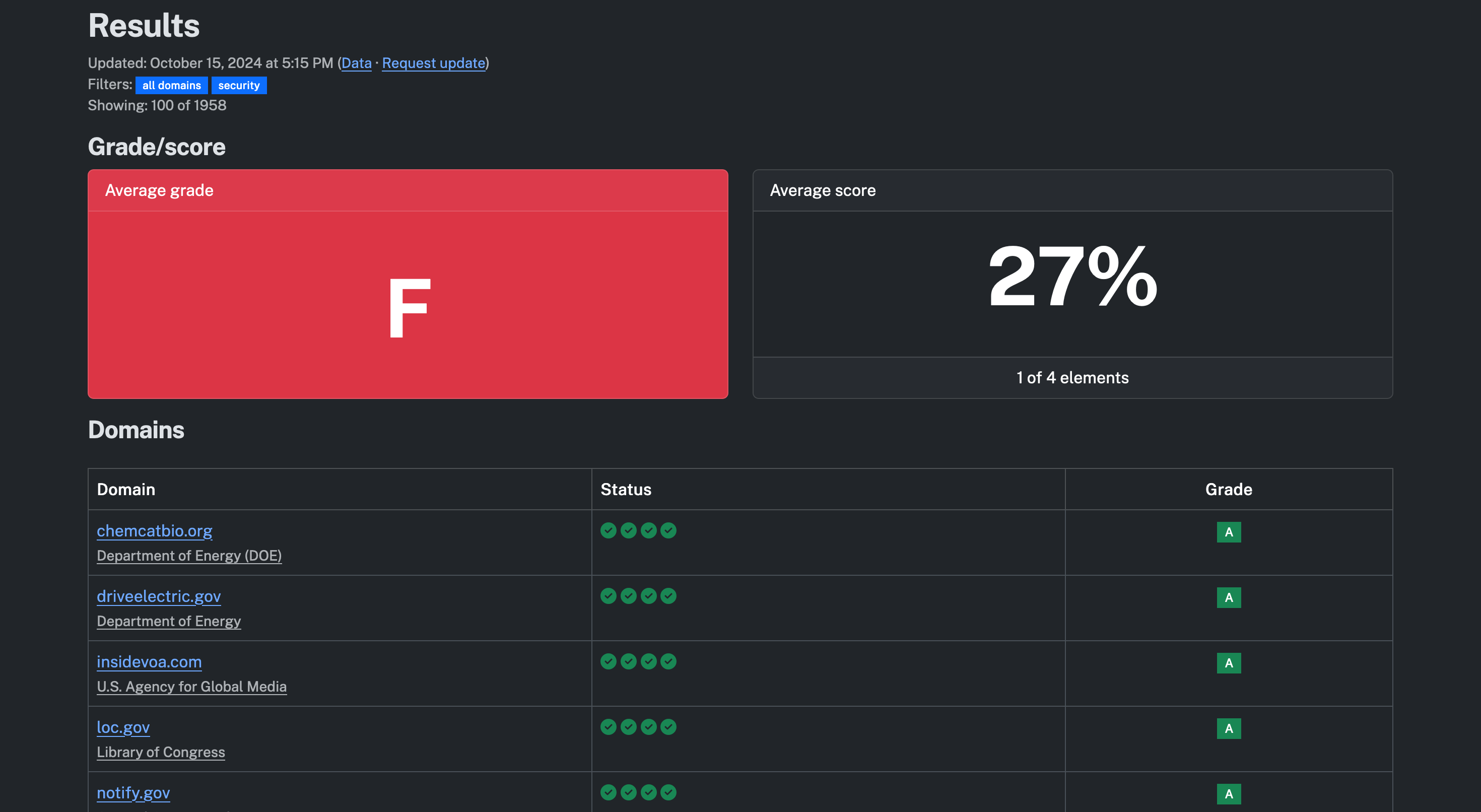
Grades
Overall average grade was an ‘F’. Federal websites received an average score of 25% and states 31%.
Seven federal websites received an ‘A’. No state websites scored an ‘A’, however, five received a ‘C’.
Content Security Policy
Content Security Policy is a security feature that defines rules for safe content and protects websites from attacks like XSS and clickjacking.
“Website owners should also consider implementing a CSP,” says the Cybersecurity and Infrastructure Security Agency in a website security blog post. “Implementing a CSP lessens the chances of an attacker successfully loading and running malicious JavaScript on the end user machine.”
HTTP Strict Transport Security
The Office of Management and Budget Memorandum M-15-13 requires agencies to encrypt HTTP traffic that travels over the public internet to or from a federal system, using HTTPS and HTTP Strict Transport Security.
“Websites and services available over HTTPS must enable HTTP Strict Transport Security (HSTS)12 to instruct compliant browsers to assume HTTPS going forward,” says OMB. “This reduces the number of insecure redirects, and protects users against attacks that attempt to downgrade connections to plain HTTP.”
According to CIO.gov, “The policy should be deployed at https://domain.gov, not https://www.domain.gov.”
X-Content-Type-Options
X-Content-Type-Options prevents sites from masking a file type. cloud.gov sets this by default if applications do not already have it. It is also recommended by Open Worldwide Application Security Project, or OWASP, as part of its security headers project.
security.txt
security.txt is a text file located on the site root-level or /.well-known/ directory that helps improve vulnerability disclosure by giving security researchers clear contact and reporting information. security.txt is an accepted standard (RFC 9116) by the Internet Engineering Task Force.
“In an effort to accelerate the delivery of all notifications, CISA supports using the ‘security.txt’ standard to streamline notifications and reduce the risk of compromise,” says CISA. “It not only helps our work but also supports other partners that try to warn organizations of internet-accessible vulnerabilities susceptible to cyber threat actors – this is most important for organizations aligned to our most valuable critical infrastructure sectors.”
CISA also recommends security.txt in its Cross-Sector Cybersecurity Performance Goals: “All public-facing web domains have a security.txt file that conforms to the recommendations in RFC 9116.”